The InterPlanetary File System (IPFS) is a content-addressed peer-to-peer file sharing network from Protocol Labs being exploited by cybercriminals to host phishing sites and other malicious content. Often associated with the web 3.0 movement, it allows its users to upload, share, and download files across a distributed worldwide network.
Gateways make IPFS accessible to the broader public, allowing pages powered by IPFS to be visited in traditional web browsers and shared with potential victims. Netcraft first detected cyber attacks using IPFS in 2016, and now detects and blocks hundreds of attacks using IPFS gateways every day.
This blog post describes what IPFS is and how it works, how and why it is used by cybercriminals, and what Netcraft is doing to block and disrupt attacks that leverage the IPFS network.
What is IPFS?
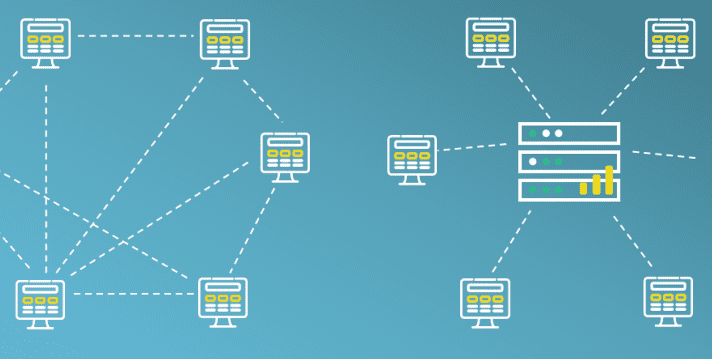
IPFS is a decentralized storage and delivery network technology. Unlike the traditional web, where most content is hosted on dedicated servers, IPFS is peer-to-peer, which means there is no single server providing each page. Instead, content is accessed via any peer (also known as a node) that has a copy of the content, with little distinction between servers and users.
The decentralized structure allows users to host or share content with increased availability and resilience. Filecoin, a cryptocurrency which builds upon IPFS to incentivize node operators to host content, is significantly cheaper than using cloud storage services like Amazon S3 at the time of writing. Eliminating the need for a single server also means content can be accessed from nodes hosted in a wide variety of locations in multiple jurisdictions—improving availability but making it more difficult to remove content.
How does IPFS manage content?
The traditional web is location-addressed: URLs, such as https://www.netcraft.com, are used to access content from a specific location. IPFS is instead content-addressed. Files are addressed with a unique content identifier (CID), a cryptographic hash of the contents of the file. The same file always has the same cryptographic hash, no matter where it is stored.
When a user fetches a file from IPFS, they retrieve the content from another node that has that file, cache it, and can make it available for other nodes on the network. Any user in the network can serve content to any other user by its content address. Nodes may also pin content, which ensures it is not removed from the node’s cache; it becomes permanently available as long as at least one node with it pinned is online.
IPFS gateways
There are several ways to access content using IPFS:
- Installing and configuring a local IPFS node.
- Using a web browser that supports the IPFS protocol natively, such as Brave.
- Using gateways, which allow users to conveniently access IPFS content over HTTPS with a traditional web browser.
The official IPFS GitHub account maintains a list of IPFS gateways. At time of writing there are less than 100 gateways in the list, of which 20 or fewer are currently online. There are a few mainstream providers that stand out, including Fleek, Cloudflare, and ipfs.io, run by Protocol Labs itself.
IPFS in phishing attacks
Cybercriminals exploit IPFS’s characteristics for nefarious purposes. Criminals can place content on the IPFS network at low cost, or even for free. Writable gateways and pinning services allow criminals to place content on the network without setting up their own infrastructure. IPFS’s decentralized nature makes it difficult to completely remove criminal content from the network, as it must be purged from every node hosting or caching it.
However, as most would-be visitors do not have native IPFS support in their web browsers, criminals will link to an IPFS gateway instead. For example, the following IPFS phishing site targeted Microsoft using the ipfs.io gateway run by Protocol Labs:
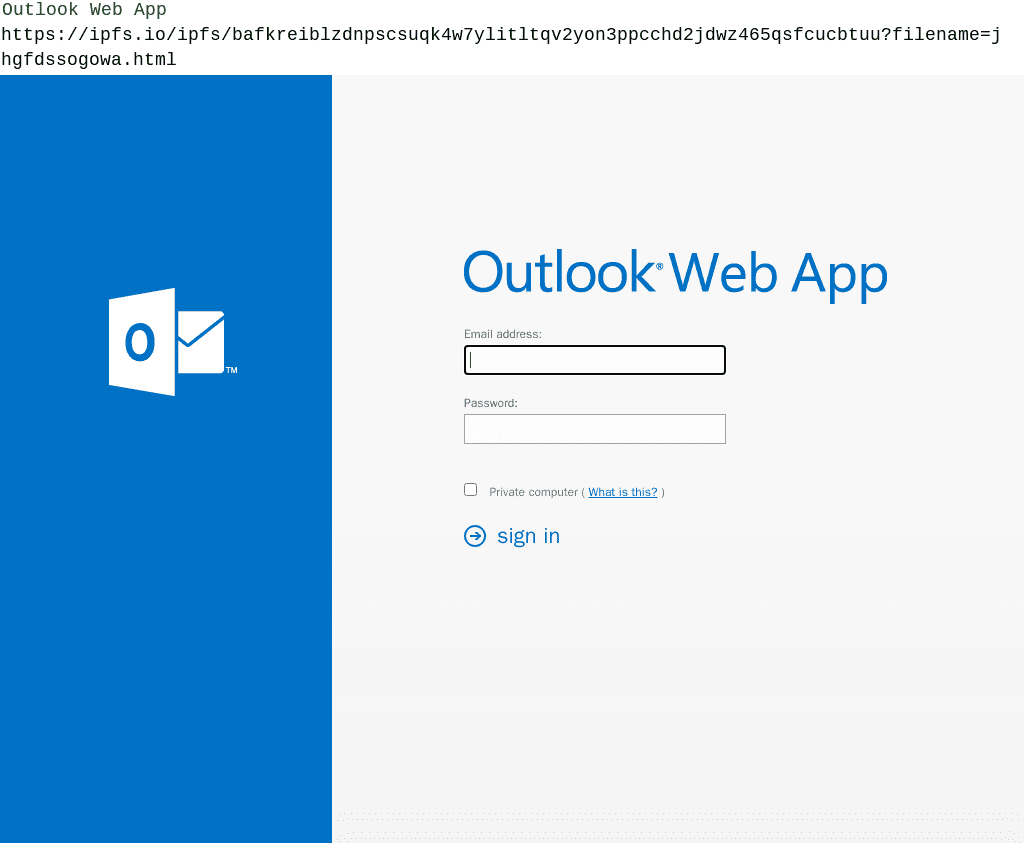
IPFS gateways are centralized and are therefore a focal point for disruption: gateway operators will typically act against malicious content by blocking it from being accessed via their gateway. Cybercriminals are forced to choose between using native IPFS links, which significantly limits the number of victims who can access the attack, or using gateways, which allows distribution to a wide range of victims but limits the duration of the attack.
As IPFS is content-addressed, pages hosted on the IPFS network are static, although they can run JavaScript. Cybercriminals must therefore use separate infrastructure to deliver stolen credentials back to themselves. Common mechanisms include sending credentials to separate drop sites on the traditional web or to Telegram channels; both strategies are also used by traditional phishing sites. Taking down the drop site or Telegram channel will also disrupt the attack on IPFS, preventing further credentials from reaching the cybercriminal.
IPFS gateway impersonation
Netcraft has also identified the existence of cybercrime hosted on domain names that impersonate IPFS gateways: while at first glance the phishing URL contains an IPFS content hash, the website is not a functioning gateway and does not allow any other IPFS hashes to be fetched. The cybercriminal operating the site could falsely claim that they don’t host the criminal content directly and merely proxy it, to deter further attention and disruption.
How is Netcraft disrupting IPFS-based attacks?
Netcraft first detected a malicious site using IPFS in 2016, and our position at the epicenter of the battle against cybercrime allows us to detect and block hundreds of malicious pages hosted on the IPFS network every day. We have also taken down over 15,000 malicious URLs confirmed to be accessible via IPFS gateways. Netcraft’s browser extension and apps block the IPFS threats described in this post, and we will block new threats as we discover them.
IPFS gateway providers can use Netcraft’s threat intelligence feeds to block access to malicious IPFS hashes as soon as they are detected by Netcraft. Netcraft’s feeds are widely licensed by browsers and antivirus companies, protecting billions of people against attacks, often within minutes of detection.
Brands targeted by IPFS-based attacks using gateways can use Netcraft’s disruption and takedown service to ensure that malicious content is blocked and removed quickly and efficiently. Contact us to learn more.