Ahead of the EU’s Digital Market Act forcing Apple’s hand to permit alternative app download options, is the amount of malware in the existing grey-market for sideloading iPhone apps a portent for things to come? Or has Apple’s approach, despite its controversy, hit the right balance to keep iPhone users secure?
On 7th March, the European Union’s Digital Market Act (DMA) comes into effect, designed to encourage fair competition across key digital platforms within the single market. The regulation compels Apple (and other “gatekeepers”) to open their platforms to third parties.
Unlike Android where supported alternatives to the Google Play Store already exist—through third party stores like Amazon Appstore and directly downloading apps from the web, known as “sideloading”—iPhone has no authorized alternative to Apple’s App Store.
As part of its planned response to the DMA, for the first time Apple is set to allow EU-based iPhone users to install apps outside its own App Store from third-party marketplaces. Apple remains at pains to point out the risks of this approach to iPhone users, echoing its 2021 position paper on the risk of sideloading.
The current state of grey-market iOS sideloading methods may explain some of Apple’s hesitancy. Misusing functionality intended for developers, current alternative marketplaces for iOS offer modified versions of popular apps with pirated content, additional or removed features, ads removed, or privacy features adjusted. In a recent study, Netcraft identified malware in around 5% of sampled iOS apps on third-party marketplaces.
At first glance, these changes appear to be a considerable risk for Apple. However, Apple’s proposed solution keeps them in the driver’s seat with the ability to review all apps—whether distributed through Apple’s own App Store or third-party marketplaces. This is a material improvement on the current sideloading scene on iOS and gives Apple much more control. However, whether the EU will accept Apple’s interpretation—seen by some as insufficient to comply with the DMA—is yet to be seen in the coming weeks.
This blog post explores these trade-offs, highlights malicious sideloaded apps, and the potential impact for Apple and the millions of iPhone users in the EU and further afield.
“Difficult trade-offs”
Within Apple’s response to the EU Digital Markets Act, it announced several security measures designed to retain control over apps released for iPhone (notably iPadOS is not included). All apps distributed via the authorized third-party app stores will have to go through a notarization process. This will be an enhanced version of the existing notarization process for third-party apps on macOS, which will check apps for malware, functionality, safety, privacy, and metadata accuracy. Apple states this will be achieved through automated processes with additional human input.
The EU will only assess Apple’s plan for compliance after the law comes into effect, which will include taking feedback from third parties. It has publicly stated that it will take “strong action” if the proposed solutions are “not good enough“.
In addition to the EU, other jurisdictions, including Japan and the UK, continue working on similar legislation with all eyes on the outcomes and determinations made by the EU and Apple’s compliance with new requirements.
Sideloading and malicious apps
Sideloading describes the act of installing an application on a device directly without using the device’s official application distribution method. So, for iPhone users, sideloading involves installing an app on their device without using Apple’s App Store.
Right now, there are already options for iPhone users—both inside and outside the EU—to sideload apps The most accessible option involves using the same mechanisms designed for developers to install their own apps onto iOS for development and testing purposes.
Several platforms have been created (such as AltStore and Sideloadly) that take advantage of these developer mechanisms to create consumer-facing third-party app stores, albeit with some friction involved. A computer must be connected to the device during installation, apps must be updated weekly to remain installed and a maximum of three such apps can be installed at once. Other options that require jailbreaking the device are far less accessible.
These platforms allow users to download and install any app from the web, and web searches reveal many sites that allow users to download apps for the purposes of sideloading on iOS. Looking at 20 popular sites found by Netcraft, we have identified over 1,000 apps impersonating popular brands, including YouTube, Instagram, Facebook, Spotify, Snapchat, TikTok, WhatsApp, X, Roblox and Tinder.
Many of these apps have been modified to unlock paid features or add extra functionality, such as customizing the app layout, removing in-app ads, and disabling sending read receipts in messaging apps. We have seen paid-for versions of TikTok being offered with subscription tiers reaching over $50 per year.
Netcraft researchers downloaded 350 apps from these sites and analyzed them for malicious content: 14 (around 5%) appeared to be malicious, including prominent examples from CyPwn and Starfiles.
Figure: istore-plus[.]net selling subscriptions to access a modified version of TikTok (Arabic left, English translation right)
However, malware targeting iOS is not exclusive to sideloaded apps and has repeatedly been found on the official iOS App Store. One of the most prominent cases occurred in 2015, where 128 million users downloaded 2,500 infected apps from the iOS App Store that contained the XcodeGhost malware. Several years later, in 2022, Meta publicly warned about 47 malicious apps on the iOS App Store targeting its users.
This problem still exists, albeit currently at low volume. In the past 6 months, Netcraft has identified fewer than 50 malicious apps on the iOS App Store on behalf of its customers, all impersonating popular brands. Netcraft identified a similar order of magnitude of malicious apps on the official Google Play Store.
Outside of the Play Store, the situation is very different., Netcraft has performed takedowns for over 21,000 apps hosted on third-party Android app stores in the past year—many being legitimate apps cloned without permission. Herein lies some of the risk from which Apple claims to be defending its users.
Apple’s proposed model for third party stores materially alters the status quo on iOS and Android: Apple will retain control over malware scanning for all apps (something Google has rolled out in India, but not yet globally) and has put up significant roadblocks to third party marketplace creation. However, this style of notarization process already protects macOS, with a senior Apple employee stating, “And as I say, today, we have a level of malware on the Mac that we don’t find acceptable and is much worse than iOS”.
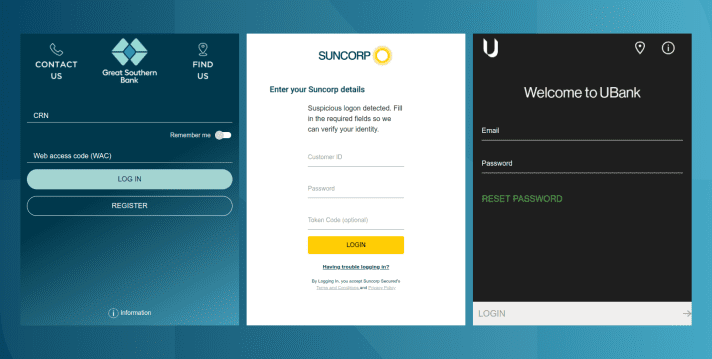
Figure 2 Fake login screens overlayed on top of legitimate banking apps, designed to collect victim’s login and password details
DMA and third-party Apple stores
Given that Apple announced these proposed changes in February, it is unlikely that Apple will designate many official third-party stores on the day that iOS 17.4 is released in March. However, it is expected on release day there will be a surge in interest amongst iOS users seeking to sideload apps both within and outside the EU.
This surge in interest could spill over into existing sideloading solutions, like AltStore and Sideloadly, which give users access to external sources riddled with malicious apps. AltStore has also announced it plans to launch an authorized alternative app store, which will likely trigger interest in the existing version of AltStore.
Closing thoughts
With the EU so far giving nothing away in terms of how it will respond to Apple’s proposals, it’s difficult to predict exactly how the iOS app ecosystem will change in the coming months and years. However, with other countries considering similar legislation, you can expect this to be the first of many changes to come.